2019-10-16 - Proofpoint - Contributor
2019-01-09 - Proofpoint - Contributor
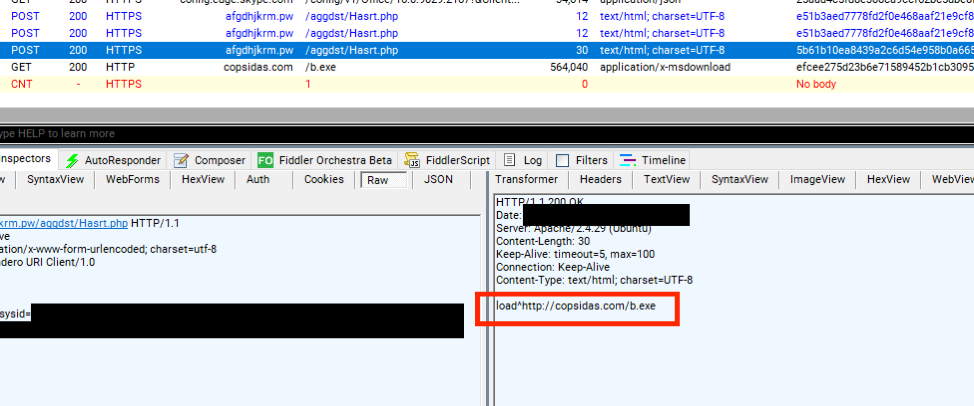 ServHelper and FlawedGrace - New malware introduced by TA505
Read More ›
ServHelper and FlawedGrace - New malware introduced by TA505
Read More ›
2018-11-13 - Google - Contributor
 Taking down a major ad fraud operation through industry collaboration
Read More ›
Taking down a major ad fraud operation through industry collaboration
Read More ›
2018-10-23 - Proofpoint - Contributor
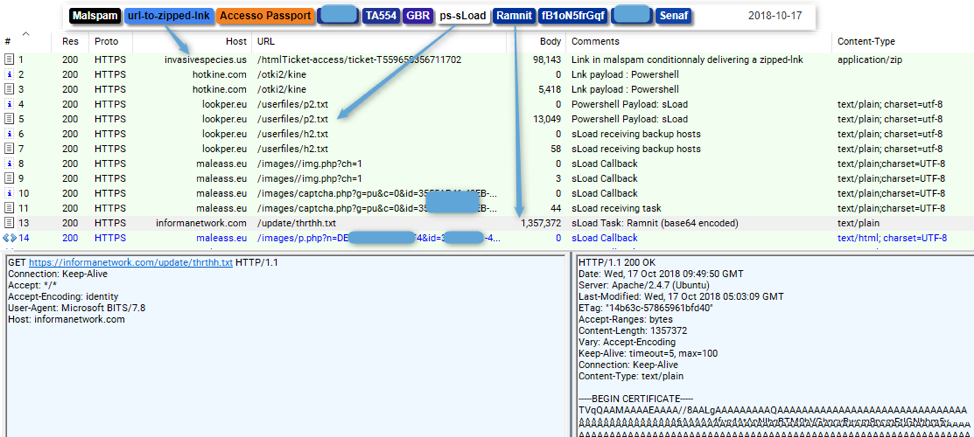 Describe sLoad campaigns by an actor with long history of activity, including the personalization of email messages with the recipient's name and address
Read More ›
Describe sLoad campaigns by an actor with long history of activity, including the personalization of email messages with the recipient's name and address
Read More ›
2018-07-24 - Proofpoint - Contributor
 An evolution of Kronos hiding behind Tor appeared. Osiris?
Read More ›
An evolution of Kronos hiding behind Tor appeared. Osiris?
Read More ›
2018-04-12 - Proofpoint - Author
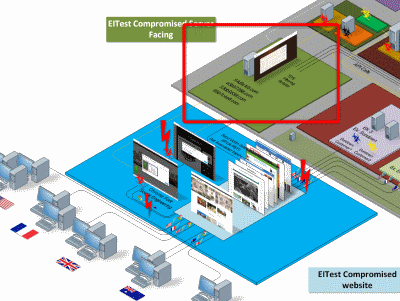 EITest, the oldest infection chain of its kind has been sinkholed.
Read More ›
EITest, the oldest infection chain of its kind has been sinkholed.
Read More ›
2018-03-29 - Proofpoint - Author
 Another (Not Darkcloud/Fluxxy) Fast Flux infrastructure emerges.
Read More ›
Another (Not Darkcloud/Fluxxy) Fast Flux infrastructure emerges.
Read More ›
2018-03-13 - Proofpoint - Author
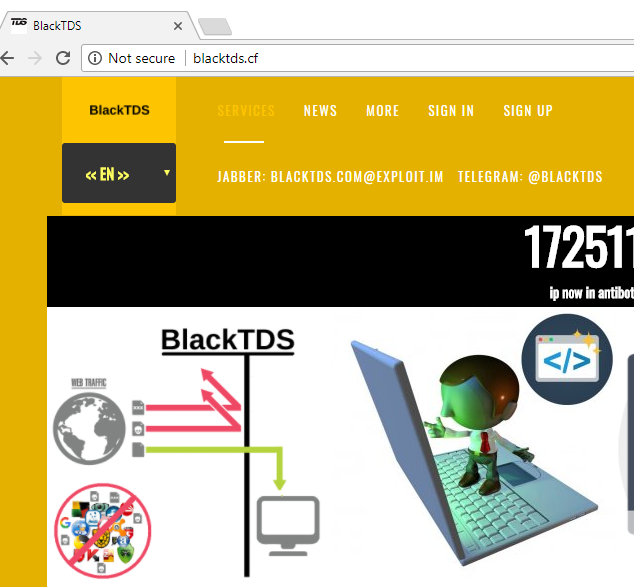 A service presented as a "Cloud TDS" is advertised underground since end of 2017.
Read More ›
A service presented as a "Cloud TDS" is advertised underground since end of 2017.
Read More ›
2018-01-31 - Proofpoint - Author
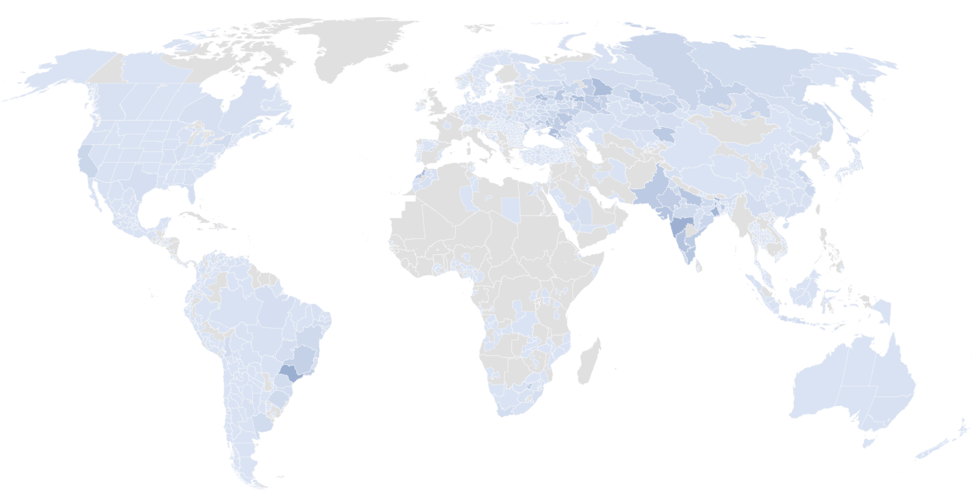 Tracking the massive Smominru botnet, the combined computing power of which has earned millions of dollars for its operators.
Read More ›
Tracking the massive Smominru botnet, the combined computing power of which has earned millions of dollars for its operators.
Read More ›
2018-01-29 - Proofpoint - Contributor
2017-11-01 - Proofpoint - Author
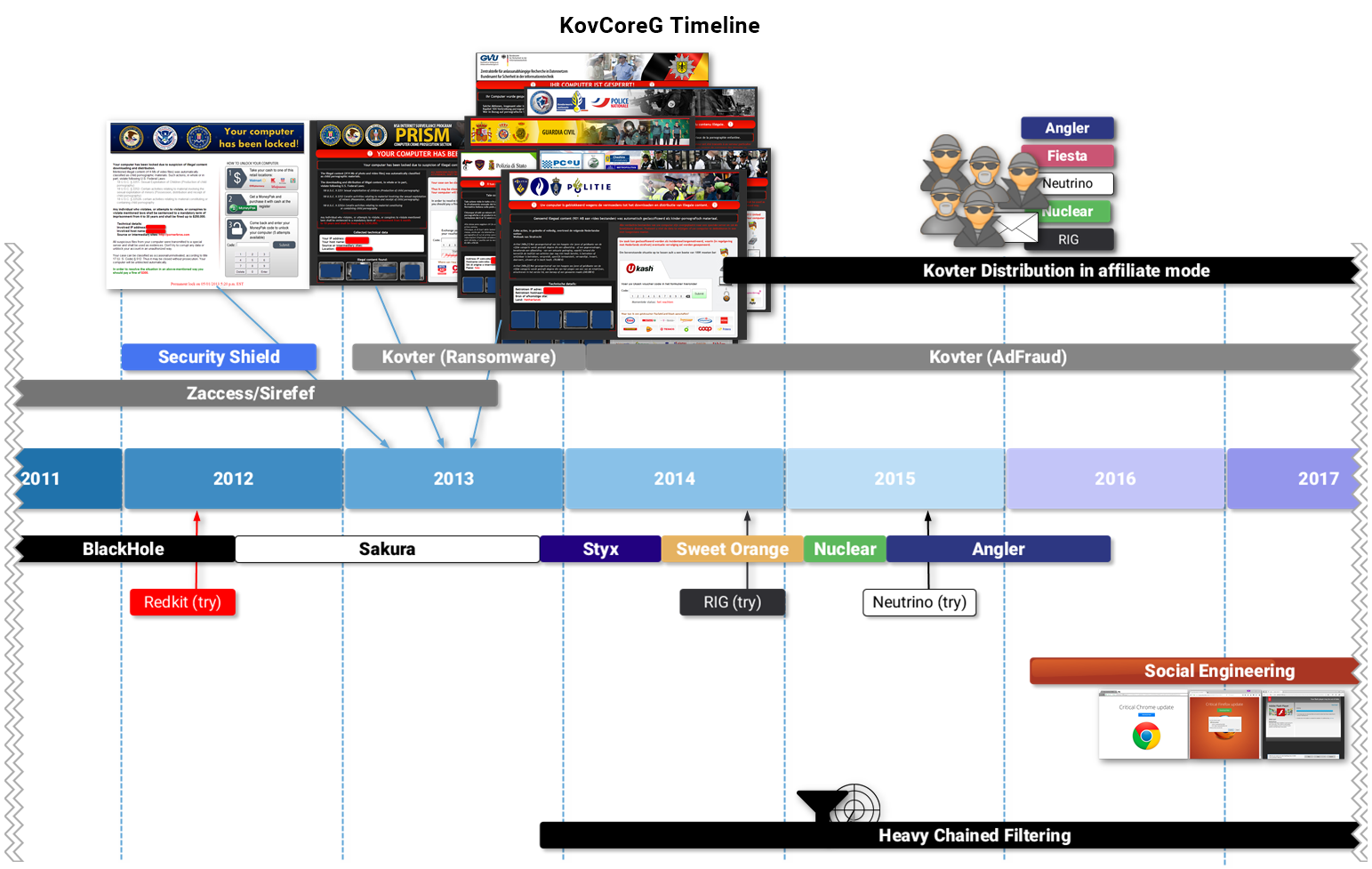 This blog traces the activities of KovCoreG, also referred to as MaxTDS by FoxIT InTELL, from its early days distributing the Zaccess backdoor to its latest social engineering attacks.
Read More ›
This blog traces the activities of KovCoreG, also referred to as MaxTDS by FoxIT InTELL, from its early days distributing the Zaccess backdoor to its latest social engineering attacks.
Read More ›
2017-08-19 - Proofpoint - Contributor
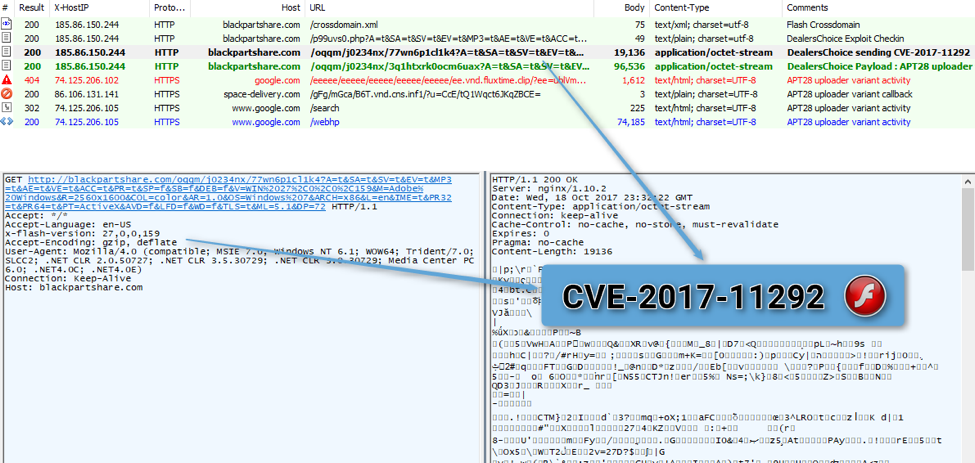 As we examined a document exploitation chain, we found that DealersChoice, the attack framework that the document uses, is now also exploiting CVE-2017-11292
Read More ›
As we examined a document exploitation chain, we found that DealersChoice, the attack framework that the document uses, is now also exploiting CVE-2017-11292
Read More ›
2017-08-06 - Proofpoint - Author
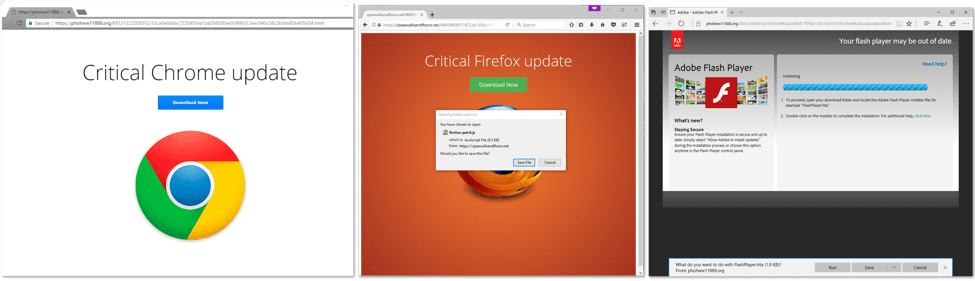 Few groups are able to infiltrate the advertising chain on the most visited websites. This post looks at a recent KovCoreG campaign and describes what we know of the current state of their very active social engineering scheme.
Read More ›
Few groups are able to infiltrate the advertising chain on the most visited websites. This post looks at a recent KovCoreG campaign and describes what we know of the current state of their very active social engineering scheme.
Read More ›
2017-08-14 - Proofpoint - Author
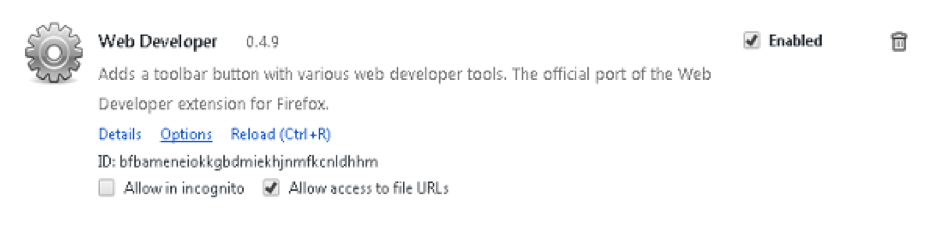 At the end of July and beginning of August, several Chrome Extensions were compromised after their author’s Google Account credentials were stolen via a phishing scheme. This resulted in hijacking of traffic and exposing users to potentially malicious popups and credential theft.
Read More ›
At the end of July and beginning of August, several Chrome Extensions were compromised after their author’s Google Account credentials were stolen via a phishing scheme. This resulted in hijacking of traffic and exposing users to potentially malicious popups and credential theft.
Read More ›
2017-06-20 - Proofpoint - Author
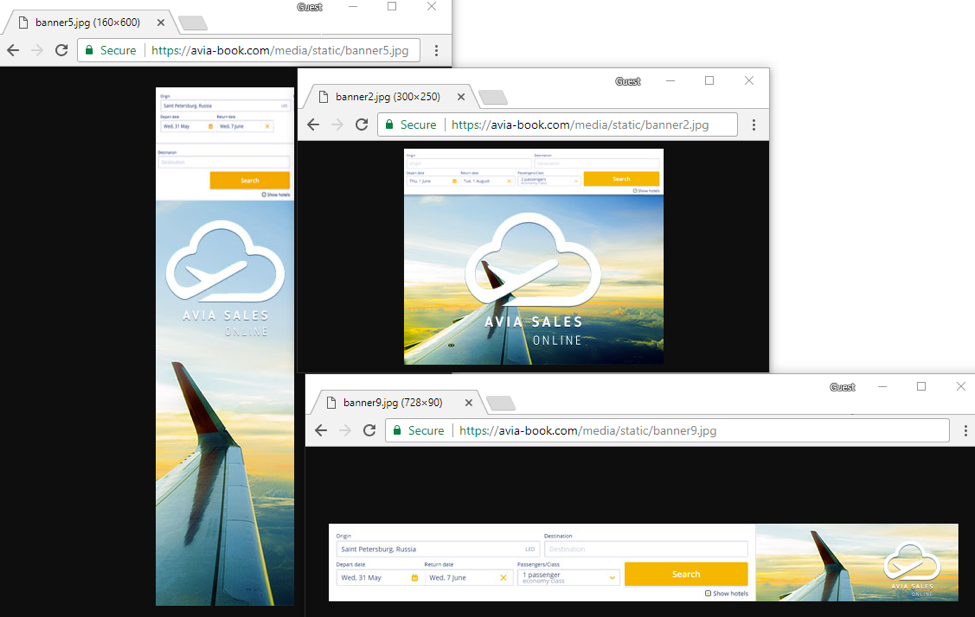 The AdGholas group has been implicated in some of the largest malvertising campaigns we have ever observed. While this group has remained active, it appears that a number of universities in the United Kingdom were recently infected with ransomware via an AdGholas infection chain, a marked departure from the banking Trojans this group usually distributes.
Read More ›
The AdGholas group has been implicated in some of the largest malvertising campaigns we have ever observed. While this group has remained active, it appears that a number of universities in the United Kingdom were recently infected with ransomware via an AdGholas infection chain, a marked departure from the banking Trojans this group usually distributes.
Read More ›
2017-05-25 - Proofpoint - Contributor
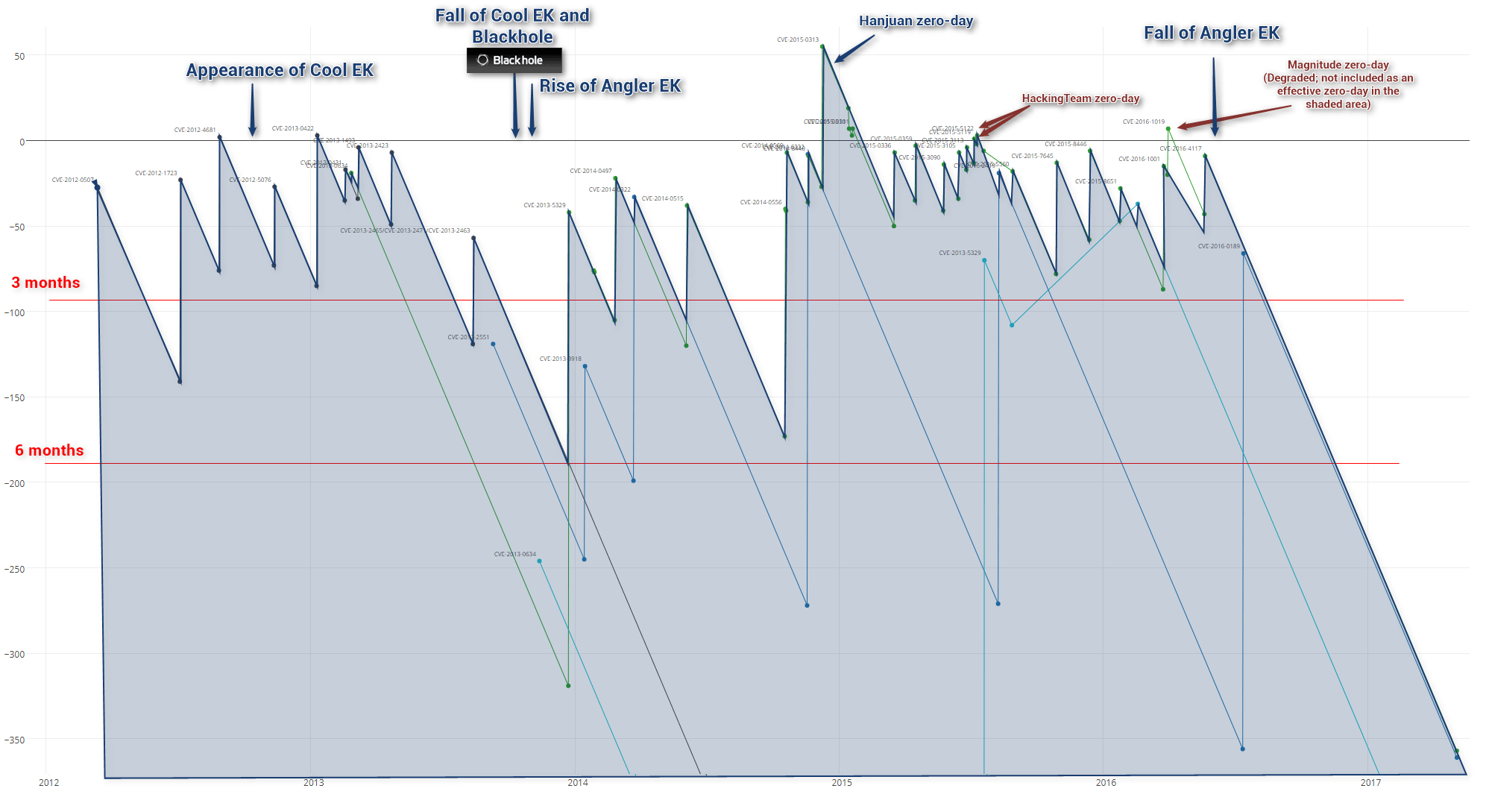 A more significant reason for the decline in EK activity is that exploitable vulnerabilities are aging quickly.
Read More ›
A more significant reason for the decline in EK activity is that exploitable vulnerabilities are aging quickly.
Read More ›
2017-05-15 - Proofpoint - Author
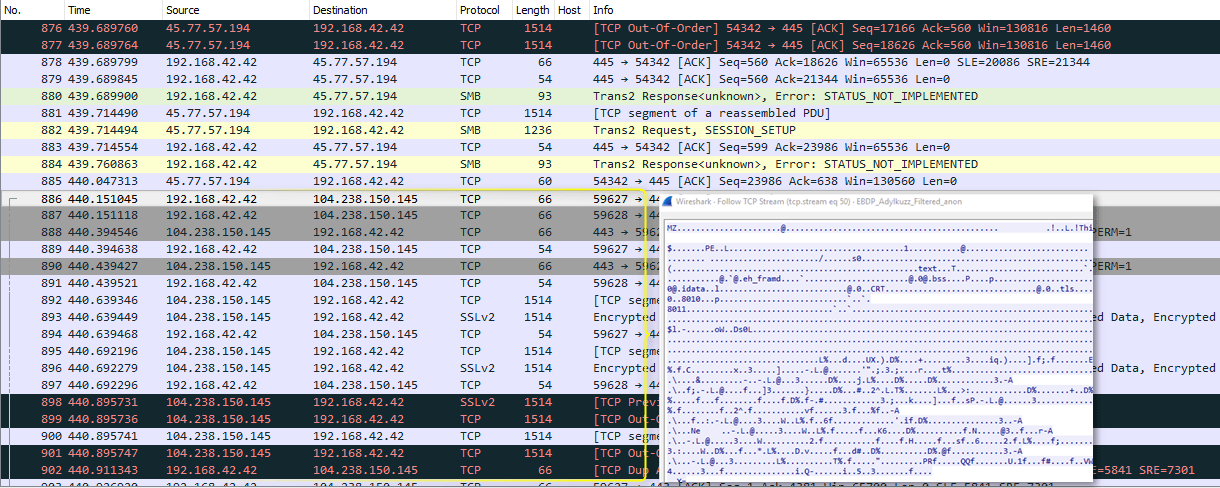 Another very large-scale attack using both EternalBlue and DoublePulsar to install the cryptocurrency miner Adylkuzz.
Read More ›
Another very large-scale attack using both EternalBlue and DoublePulsar to install the cryptocurrency miner Adylkuzz.
Read More ›
2017-01-17 - Proofpoint - Author
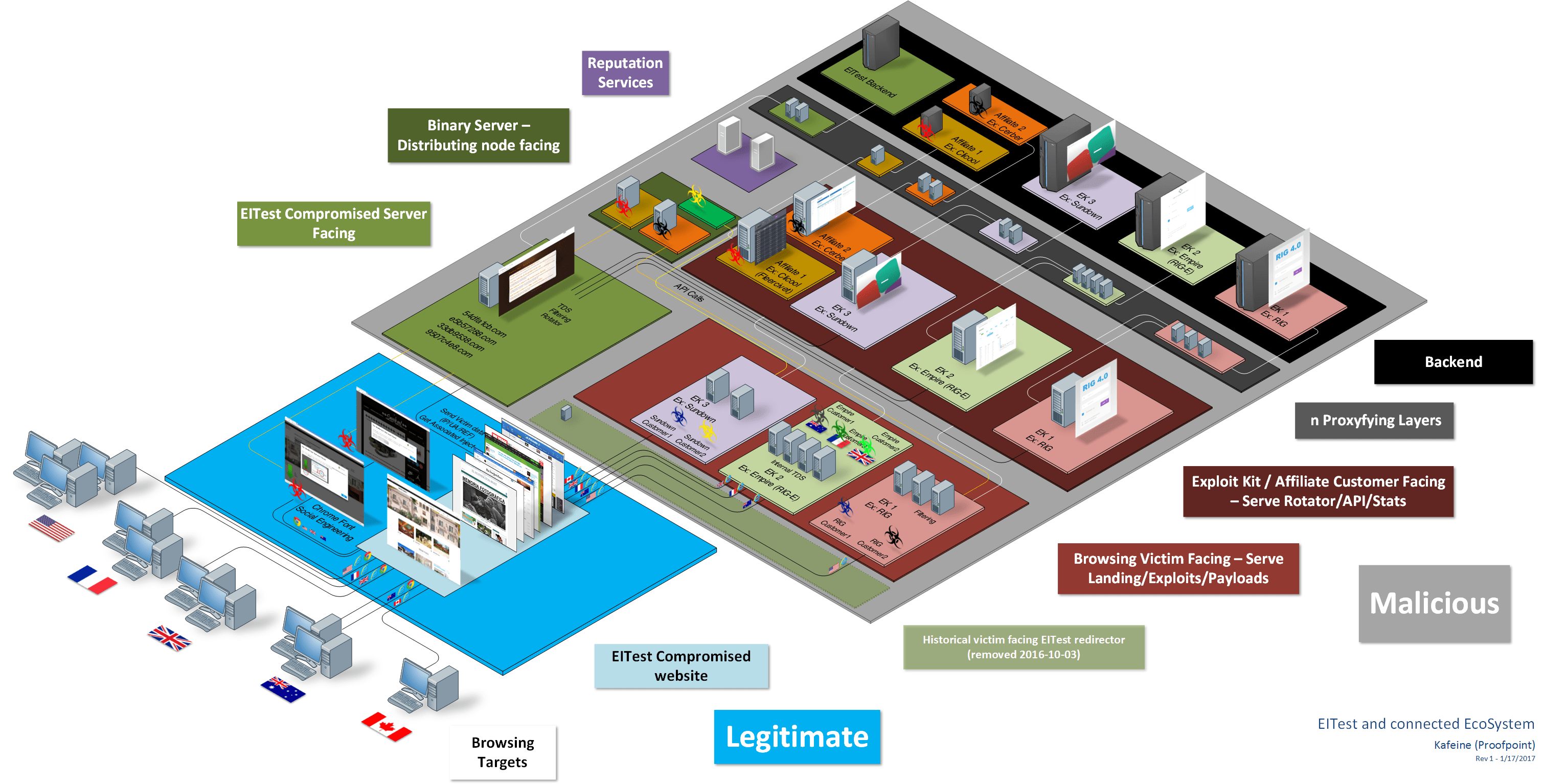 “EITest” is a well-documented infection chain that generally relies on compromised websites to direct users to exploit kit landing pages.
Read More ›
“EITest” is a well-documented infection chain that generally relies on compromised websites to direct users to exploit kit landing pages.
Read More ›
2016-12-13 - Proofpoint - Author
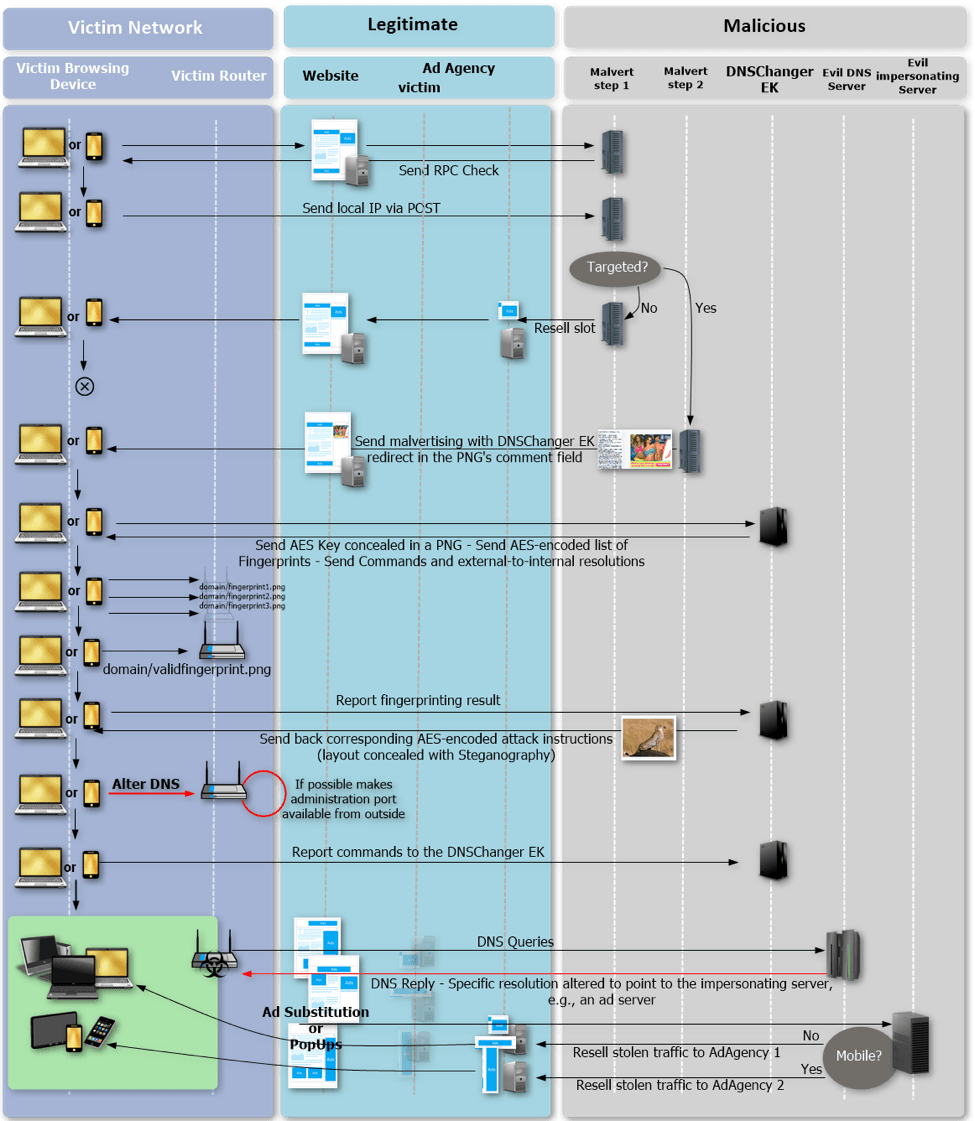 An improved version of the “DNSChanger EK” used in ongoing malvertising campaigns.
Read More ›
An improved version of the “DNSChanger EK” used in ongoing malvertising campaigns.
Read More ›
2016-11-14 - Proofpoint - Author
2016-09-13 - Proofpoint - Author
2016-08-11 - Proofpoint - Author
2016-07-28 - Proofpoint - Author
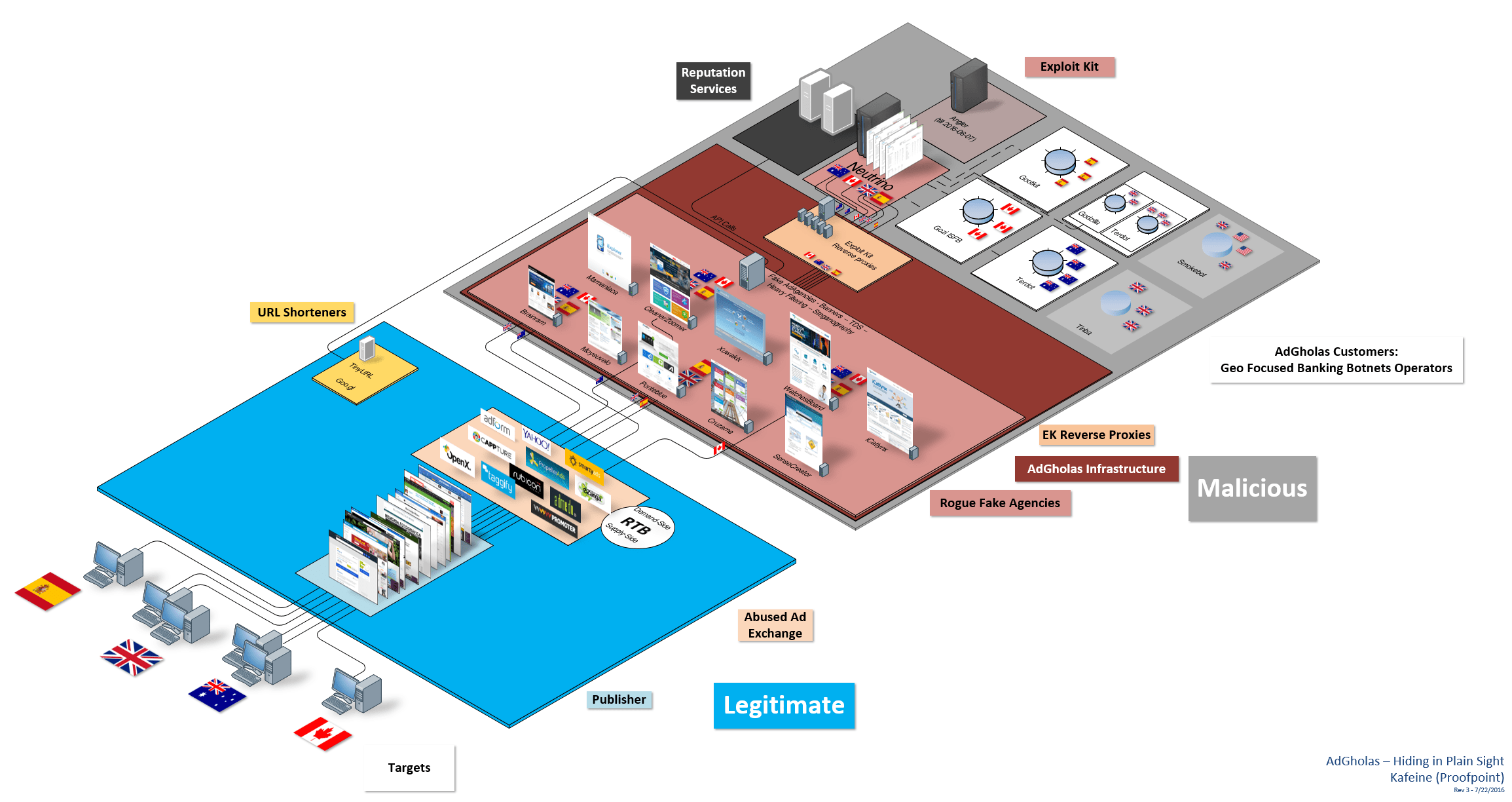 A massive malvertising network operating since 2015. Run by a threat actor we designated as AdGholas and pulling in as many as 1 million client machines per day.
Read More ›
A massive malvertising network operating since 2015. Run by a threat actor we designated as AdGholas and pulling in as many as 1 million client machines per day.
Read More ›
2016-07-11 - Proofpoint - Contributor
2016-05-09 - Proofpoint - Contributor
2016-04-08 - Proofpoint - Author
2016-03-18 - Proofpoint - Author
2016-03-10 - Proofpoint - Contributor
2015-12-15 - Proofpoint - Author
2016-02-16 - Proofpoint - Contributor
2015-08-27 - Proofpoint - Contributor