2012-11-09 - Eolution
Cool EK : “Hello my friend...” CVE-2012-5076
If you follow this blog you'll get fast sick of Cool EK and Reveton.
The Cool EK of Reveton distributors (yes it's also used by other groups, for instance the CBeplay.P ransomware distributors) is moving a lot.
Hunting for the Adobe Reader XI 0 day announced by Brian Krebs, I found a 0.7.9 PluginDetect...
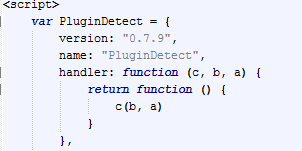 |
| PluginDetect 0.7.9 on Cool EK |
that whispered me
 |
| "new" jar file on Cool EK |
to check the exploit kit with Java 1.7 update 7 and....Hello my friend...the 0 day after you know...the previous 0 day (read : CVE-2012-5076 after CVE-2012-4681)
 |
| From "Battlefield" to "Hello my friend..." |
<edit1 :
Note: I presumed it was CVE-2012-5067 as : it's not working on j7u9, it's working on j7u7...it could be something else thought chances were low... I was wrong. see at the end. />
<edit5:>
Cool EK infecting Windows 7 x64 via IE9 plugin Java 7u7 and pushing Reveton Ransomware which gather it's Turkish disguise from its C&C
</edit5>
 |
| Cool EK (Reveton distributor version) CVE-2012-5076 Path |
 |
| Java 1.7 u7 on IE9 - Win7 |
With same configuration (j7u7 + IE9 + Win7) on Cool EK from CBeplay.P distributors you'll get :
 |
| CBeplay.P Cool EK : No CVE-2012-5076 path |
Here is the CVE-2012-5076 working path :
http://193.1xx.120.xx/r/l/***_sessions_****.php (including plugin detect 0.7.9 )
http://193.1xx.120.xx/r/64size_font.eot - ee1ed92474bd1de3093d056d8c4404ff (Font from duqu like drop)
http://193.1xx.120.xx/r/l/getJavaInfo.jar - fad89bdfdce9322767944f0e1f15a009 (java detect)
http://193.1xx.120.xx/r/media/new.jar - 327a1cbf1e1e06df765f959ad5b05089 ( CVE-2012-5076)
http://193.1xx.120.xx/r/f.php?k=2&e=0&f=0 - 746d7f49ceadf9315b31957f5da32fb1 (Reveton - no bypass proxy as we saw in last path of CVE-2012-4681)
<edit2: 17:59 09/11/12>
With some help , am able to put more information about this jar file.
The bagdfssdb.class is encrypted with ZelixKlassMaster
So we have to take a look at the method clinit to find the key :
0000004E : tableswitch l: 0, h: 3, def: pos.00000080, pos.(0000006C, 00000071, 00000076, 0000007B)
0000006C : bipush 55
0000006E : goto pos.00000082
00000071 : bipush 120
00000073 : goto pos.00000082
00000076 : bipush 64
00000078 : goto pos.00000082
0000007B : bipush 24
0000007D : goto pos.00000082
00000080 : bipush 81
Applying a SUB of 0x2a we get payload.class ( 9b7481ce8aa6844e25c196c13d9250d9 ) :
</edit2>
What about the % break. It seems it double the rate...but starting from around 6% we are now to something around 12%. As usual it's always difficult to talk about that, as the % depends of the traffic/country..etc
In Turkey, before this CVE, break % could reach 20% where rate for Germany was between 3 and 5%
With some help , am able to put more information about this jar file.
The bagdfssdb.class is encrypted with ZelixKlassMaster
So we have to take a look at the method clinit to find the key :
 |
| Method: <clinit> in bagdfssda |
0000004E : tableswitch l: 0, h: 3, def: pos.00000080, pos.(0000006C, 00000071, 00000076, 0000007B)
0000006C : bipush 55
0000006E : goto pos.00000082
00000071 : bipush 120
00000073 : goto pos.00000082
00000076 : bipush 64
00000078 : goto pos.00000082
0000007B : bipush 24
0000007D : goto pos.00000082
00000080 : bipush 81
Using the zkm_decrypt.py provided with DirtyJOE and the key [55,120, 64, 24, 81]
 |
| zkm_decrypt.py loaded in DirtyJOE |
 |
| Decrypted |
Applying a SUB of 0x2a we get payload.class ( 9b7481ce8aa6844e25c196c13d9250d9 ) :
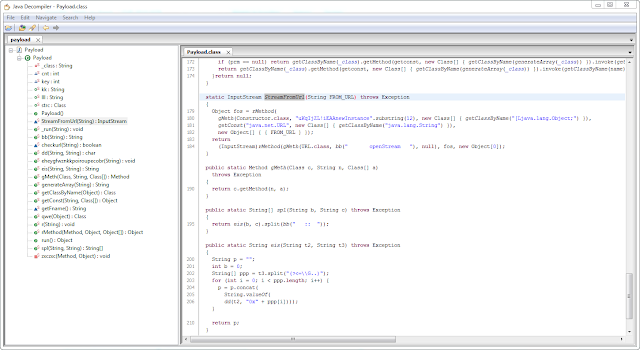 |
| Payload class in Java Decompiler. |
</edit2>
What about the % break. It seems it double the rate...but starting from around 6% we are now to something around 12%. As usual it's always difficult to talk about that, as the % depends of the traffic/country..etc
In Turkey, before this CVE, break % could reach 20% where rate for Germany was between 3 and 5%
Be ready to see same kind of post for Blackhole 2.0 (or update to 2.1) soon, as chances are HUGE that Paunch is indeed behind Cool EK code.
Others changes : Old Flash exploit activated (/media/score.swf ), old PDF exploits added ( /media/pdf_old.php vs /media/pdf_new.php).
I won't spend time on this (at least right now)
Others changes : Old Flash exploit activated (/media/score.swf ), old PDF exploits added ( /media/pdf_old.php vs /media/pdf_new.php).
I won't spend time on this (at least right now)
Read more ?
A technical analysis on new Java vulnerability (CVE-2012-5076) - 15-11-2012 - Jeong Wook (Matt) Oh - MMPC
About Cool EK :
A technical analysis on new Java vulnerability (CVE-2012-5076) - 15-11-2012 - Jeong Wook (Matt) Oh - MMPC
About Cool EK :
Cool Exploit Kit - A new Browser Exploit Pack on the Battlefield with a "Duqu" like font drop
About CVE and EK/BEP:
An Overview of Exploit Packs (Update 17) October 12, 2012 - Mila - Contagio
About decrypting ZKM :
http://code.google.com/p/corkami/wiki/Java Ange Albertini - corkami - 07-11-2011
http://dirty-joe.com/help/python_scripting.php
Post Publication :
CVE-2011-3402 and Cool Exploit Kit - 2012-11-28 - yomuds - a bunch of random security bits!
<Edit 1: 13:14 09/11/12>
Removed the references to CVE-2012-5067About CVE and EK/BEP:
An Overview of Exploit Packs (Update 17) October 12, 2012 - Mila - Contagio
About decrypting ZKM :
http://code.google.com/p/corkami/wiki/Java Ange Albertini - corkami - 07-11-2011
http://dirty-joe.com/help/python_scripting.php
Post Publication :
CVE-2011-3402 and Cool Exploit Kit - 2012-11-28 - yomuds - a bunch of random security bits!
<Edit 1: 13:14 09/11/12>
Thanks to Timo Hirvonen from F-Secure for pointing me to the correct CVE associated to this exploit.
</edit1><edit2: more information on this Jar file.
Thanks to Ange Albertini for his help.
</edit2>
<edit3>
I don't want to be guilty for an integration of this CVE in other Exploit Pack.
So don't expect freely avaiblable files from me as long as it's not widely used.
Password protected file :
http://goo.gl/TMXwx (dropbox)
http://goo.gl/ElxSO (Mega)
kafeine at dontneedcoffee dot com for password.
No need to mail if you are not ready to give real name and company
</edit3>
<edit4 Jar image blurred.
Thanks to Michael Schierl
</edit4>
<edit 5 : Link in video dead, here is it. For those who do not like blur and so on :
In war, whatever your weakness/strengths are, better not help other side improve its weapons.</edit5>




